The Health Insurance Portability and Accountability Act (HIPAA) sets the standard for sensitive patient data protection. Companies that deal with protected health information (PHI) must have physical, network, and process security measures in place and follow them to ensure HIPAA Compliance. Covered entities (anyone providing treatment, payment, and operations in healthcare) and business associates (anyone who has access to patient information and provides support in treatment, payment, or operations) must meet HIPAA Compliance. Other entities, such as subcontractors and any other related business associates must also be in compliance.
According to the U.S. Department of Health and Human Services (HHS), the HIPAA Privacy Rule, or Standards for Privacy of Individually Identifiable Health Information, establishes national standards for the protection of certain health information. Additionally, the Security Rule establishes a national set of security standards for protecting specific health information that is held or transferred in electronic form.
The Security Rule operationalizes the Privacy Rule’s protections by addressing the technical and nontechnical safeguards that covered entities must put in place to secure individuals’ electronic PHI (e-PHI). Within HHS, the Office for Civil Rights (OCR) is responsible for enforcing the Privacy and Security Rules with voluntary compliance activities and civil money penalties.
HHS points out that as health care providers and other entities dealing with PHI move to computerized operations, including computerized physician order entry (CPOE) systems, electronic health records (EHR), and radiology, pharmacy, and laboratory systems, HIPAA compliance is more important than ever. Similarly, health plans provide access to claims as well as care management and self-service applications. While all of these electronic methods provide increased efficiency and mobility, they also drastically increase the security risks facing healthcare data.
The Security Rule is in place to protect the privacy of individuals’ health information, while at the same time allowing covered entities to adopt new technologies to improve the quality and efficiency of patient care. The Security Rule, by design, is flexible enough to allow a covered entity to implement policies, procedures, and technologies that are suited to the entity’s size, organizational structure, and risks to patients’ and consumers’ e-PHI.
The HHS requires physical and technical safeguards for organizations hosting sensitive patient data. These physical safeguards include…
Other technical policies for HIPAA compliance need to cover integrity controls, or measures put in place to confirm that ePHI is not altered or destroyed. IT disaster recovery and offsite backup are key components that ensure that electronic media errors and failures are quickly remedied so that patient health information is recovered accurately and intact. One final technical safeguard is network, or transmission security that ensures HIPAA compliant hosts protect against unauthorized access to ePHI. This safeguard addresses all methods of data transmission, including email, internet, or private networks, such as a private cloud.
To help ensure HIPAA compliance, the U.S. government passed a supplemental act, The Health Information Technology for Economic and Clinical Health (HITECH) Act, which raises penalties for health organizations that violate HIPAA Privacy and Security Rules. The HITECH Act was put into place due to the development of health technology and the increased use, storage, and transmission of electronic health information.
The need for data security has grown with the increase in the use and sharing of electronic patient data. Today, high-quality care requires healthcare organizations to meet this accelerated demand for data while complying with HIPAA regulations and protecting PHI. Having a data protection strategy in place allows healthcare organizations to:
The best data protection solutions recognize and protect patient data in all forms, including structured and unstructured data, emails, documents, and scans, while allowing healthcare providers to share data securely to ensure the best possible patient care. Patients entrust their data to healthcare organizations, and it is the duty of these organizations to take care of their protected health information.
A number of changes and updates to HIPAA are being considered and may become either guidance or parts of the law within the coming months. Updated Penalties for HIPAA Violations Potential fines and penalties were updated earlier in 2019. (The official documentation was scheduled to be published on April 30th.) Details outlined in the document included a tiered structure for violations with corresponding “caps” now starting from $25,000 for Tier 1.
Better Enforcement and Accountability of Violations While this isn’t a change in the legislation itself, the Health & Human Services Office for Civil Rights (HHS OCR) has tightened enforcement efforts. The increased number of violations tagged could be the reason for a record-setting year of fines levied (almost $29 million in 2018). Potential Permanent Audit Program The HHS has long spoken of a permanent audit program. When the organization launched “Phase 2” of the HIPAA audit program, it mentioned a permanent audit structure in the future. While, at the time of this writing, the audit program has not been changed to a permanent structure.
Additional Guidance or Regulations Regarding Opioids The status of opioid addiction and overuse in America has been prominently labeled as a “crisis” and an “epidemic”. New legislation has been promised and debated to battle the issues surrounding the controversial drug. However, it may cause further changes to HIPAA. These changes could range from further guidance or potential compliance issues.
COBIT (Control Objectives for Information and Related Technologies) is a framework for IT Governance and IT Management. It was developed by ISACA (Information Systems Audit & Control Association), is on its fifth iteration as of 2012 and is aimed at providing an end to end business view of the governance of enterprise IT. Its principles are based on ensuring a holistic approach to business decision making, meeting stakeholder needs, separating governance from management, covering enterprise IT from end to end and the application of a single integrated framework.
Cyber Essentials is a Government- backed and industry-supported scheme that can help your business protect itself against the growing cyber threats. Big or small, cyber essentials provides any business with the right credentials to showcase as a trustworthy and secure company. This can be beneficial in the tendering process, and help you comply and win more contracts.
Cyber Essentials is a foundation level certification designed to provide a statement of the basic controls your organisation should have in place to mitigate the risk from common cyber threats. This is achieved through a self-assessment process carried out under the guidance of our cyber security experts. Cyber Essentials Plus is an enhanced cyber security certification scheme for businesses that need more than Cyber Essentials has to offer. You can find out more about the differences between Cyber Essentials and Cyber Essentials Plus here.
If you require Cyber Essentials urgently, you can opt for our Fast Track service. With Fast Track, our team will get you through certification within 2 business days*, ensuring you can be fully certified before submitting a bid for a government tender. *Please refer to product page for timings.
Cyber Essentials Plus is designed for businesses that have matured their network infrastructure data requirements and have outgrown the minimum requirements of the basic Cyber Essentials scheme. A range of public and private sector organisations have already adopted Cyber Essentials Plus since the scheme’s inception in 2014 with large global corporates such as Vodafone and Oracle leading the way in cyber security best practice. This has led to many public sector organisations, such as the Ministry of Defence and Home Office, mandating its requirements across their respective supply chains.
Cyber Essentials certification indicates that your organisation takes a proactive stance against malicious cyber attacks. In addition, it offers a mechanism to demonstrate to customers, investors, insurers and others that you have taken the minimum yet essential precautions to protect your organisation against cyber threats. The National Cyber Security Centre states that undertaking the Cyber Essentials certification process and implementing even one of the five controls required by Cyber Essentials can protect businesses from around 80% of attacks.
This will depend on which level of Cyber Essentials you take. You will need to complete a self-assessment questionnaire which Cyber Essentials Online will review. With Cyber Essentials Plus you also undergo a more rigorous test of your organisation’s cyber security systems where our cyber security experts carry out vulnerability tests to make sure that your organisation is protected against basic hacking and phishing attacks. A full overview of Cyber Essentials is available for free in the scheme summary document.
The purpose of Cyber Essentials is to improve your organisation’s cyber-readiness. Annual certification is required. This acts as an opportunity to make sure that your security is ready to defend against 80% of all common attacks.
The UK public sector market is worth over £240 billion per annum and Cyber Essentials can support your business in its efforts to become a supplier to the public sector. Essentially the government won’t do business with you unless they know you, and the companies you do business with, are secure from cyber attack. In a speech at the Institute of Directors in March 2017, then Minister of State for Digital and Culture Matt Hancock said: “I mentioned the Government already requires many of its suppliers to hold a Cyber Essentials certificate. We’ll be strengthening this requirement to ensure even more of our contractors take up the scheme.” Since October 2014 Cyber Essentials has been mandatory for suppliers of Government contracts which involve handling personal information and providing some ICT products and services. Holding a Cyber Essentials certification enables you to bid for these lucrative contracts.
Again, this depends on which level of certification you choose to undergo. Our foundation level starts at £300 excl. VAT / year Find out more about products and prices here. HOW QUICK IS THE CYBER ESSENTIALS CERTIFICATION PROCESS? The quicker you can return your self-assessment questionnaire to us, the quicker we can turn it around. Generally, we can turn applications around quite quickly. If you’re looking to become certified in a hurry you can use our Fast Track service where we can return this to you within 2 business days*.
We can’t send the actual self-assessment form until you have signed up. However, you can download our sample questionnaire here. This document outlines the type of information you will need to gather and submit during the certification process. IS THE QUESTIONNAIRE A TICK BOX YES/ NO OR WILL IT REQUIRE LENGTHY DETAILS? The questionnaire requires answers to all questions – most of these questions will require brief notes to enable us to understand your company and the information security controls that you have in place. By providing full details in the questionnaire you will reduce the time required for certification as we will have all the information we need up front.
The Cyber Essentials application journey will differ slightly depending on whether you choose Cyber Essentials or Cyber Essentials Plus. The stages are outlined below but timescales may differ depending on the applicant’s completion of each stage. Regardless of which product level you choose, there are three clear stages you will go through in order to obtain your Cyber Essentials certification. Your Cyber Essentials purchase will grant you access to the members’ area and the self-assessment questionnaire to complete online. You do not have to complete the questionnaire in one go. You can save your questionnaire at any point, return to it later and submit for review at your leisure. However, we would advise that you complete and submit your questionnaire as quickly as possible in order to obtain your Cyber Essentials certification in the shortest possible time. This is more relevant when purchasing Cyber Essentials Plus as you will need to complete the Cyber Essentials certification process first. Once you submit your completed questionnaire via the online form we will review your application and will liaise with you regarding any gaps or additional information required in order to approve your application and submit it to the accreditation body, QG Business Solutions. If you have chosen to apply for Cyber Essentials Plus, it is at this stage that ID Cyber Solutions, our accredited certification body, will arrange a suitable date and time to visit your premises and conduct the more stringent tests required for Cyber Essentials Plus certification. The awarding body, QG Business Solutions, will then issue your certification, confirming that you are Cyber Essentials certified.
Threat actors are becoming increasingly sophisticated, motivated and well-funded, with organisations today facing many security challenges. To meet these challenges, organisations must move from a protective, reactive approach to a defensive, proactive one, otherwise known as Managed Detection and Response (MDR). Evolving security monitoring and improving not only prevention but also detection is now, more than ever, a must for organisations. CTM is NCC Group’s gateway solution to MDR, delivering an advanced 24/7 threat monitoring and detection capability out of our European Security Operations Centre (SOC). CTM has been developed over the past two decades, drawing on the experience of our threat intelligence experts, defence operations analysts, incident response investigators, forensic investigation experts and malware analysis teams. Its proven capability is based upon a combination of our unique threat intelligence and our purpose-built technology stack, supported by a global, expert security team.
An IT Security Policy identifies the rules and procedures for all individuals accessing and using an organization's IT assets and resources. An Information Technology (IT) Security Policy identifies the rules and procedures for all individuals accessing and using an organization's IT assets and resources. Effective IT Security Policy is a model of the organization’s culture, in which rules and procedures are driven from its employees' approach to their information and work. Thus, an effective IT security policy is a unique document for each organization, cultivated from its people’s perspectives on risk tolerance, how they see and value their information, and the resulting availability that they maintain of that information. For this reason, many companies will find a boilerplate IT security policy inappropriate due to its lack of consideration for how the organization’s people actually use and share information among themselves and to the public.
The objectives of an IT security policy is the preservation of confidentiality, integrity, and availability of systems and information used by an organization’s members. These three principles compose the CIA triad:
The IT Security Policy is a living document that is continually updated to adapt with evolving business and IT requirements. Institutions such as the International Organization of Standardization (ISO) and the U.S. National Institute of Standards and Technology (NIST) have published standards and best practices for security policy formation. As stipulated by the National Research Council (NRC), the specifications of any company policy should address:
Also mandatory for every IT security policy are sections dedicated to the adherence to regulations that govern the organization’s industry. Common examples of this include the PCI Data Security Standard and the Basel Accords worldwide, or the Dodd-Frank Wall Street Reform, the Consumer Protection Act, the Health Insurance Portability and Accountability Act, and the Financial Industry Regulatory Authority in the United States. Many of these regulatory entities require a written IT security policy themselves. An organization’s security policy will play a large role in its decisions and direction, but it should not alter its strategy or mission. Therefore, it is important to write a policy that is drawn from the organization’s existing cultural and structural framework to support the continuity of good productivity and innovation, and not as a generic policy that impedes the organization and its people from meeting its mission and goals.
General Data Protection Regulation (GDPR): What you need to know to stay compliant GDPR is a regulation that requires businesses to protect the personal data and privacy of EU citizens for transactions that occur within EU member states. And non-compliance could cost companies dearly. Here’s what every company that does business in Europe needs to know about GDPR.
Companies that collect data on citizens in European Union (EU) countriesl need to comply with strict new rules around protecting customer data. The General Data Protection Regulation (GDPR) sets a new standard for consumer rights regarding their data, but companies will be challenged as they put systems and processes in place to maintain compliance. Compliance will cause some concerns and new expectations of security teams. For example, the GDPR takes a wide view of what constitutes personal identification information. Companies will need the same level of protection for things like an individual’s IP address or cookie data as they do for name, address and Social Security number.
The GDPR leaves much to interpretation. It says that companies must provide a “reasonable” level of protection for personal data, for example, but does not define what constitutes “reasonable.” This gives the GDPR governing body a lot of leeway when it comes to assessing fines for data breaches and non-compliance. Time is running out to meet the deadline, so CSO has compiled what any business needs to know about the GDPR, along with advice for meeting its requirements. Many of the requirements do not relate directly to information security, but the processes and system changes needed to comply could affect existing security systems and protocols.
The European Parliament adopted the GDPR in April 2016, replacing an outdated data protection directive from 1995. It carries provisions that require businesses to protect the personal data and privacy of EU citizens for transactions that occur within EU member states. The GDPR also regulates the exportation of personal data outside the EU. The provisions are consistent across all 28 EU member states, which means that companies have just one standard to meet within the EU. However, that standard is quite high and will require most companies to make a large investment to meet and to administer. According to an Ovum report, about two-thirds of U.S. companies believe that the GDPR will require them to rethink their strategy in Europe. Even more (85 percent) see the GDPR putting them at a competitive disadvantage with European companies.
The short answer to that question is public concern over privacy. Europe in general has long had more stringent rules around how companies use the personal data of its citizens. The GDPR replaces the EU’s Data Protection Directive, which went into effect in 1995. This was well before the internet became the online business hub that it is today. Consequently, the directive is outdated and does not address many ways in which data is stored, collected and transferred today.
How real is the public concern over privacy? It is significant and it grows with every new high-profile data breach. According to the RSA Data Privacy & Security Report, for which RSA surveyed 7,500 consumers in France, Germany, Italy, the UK and the U.S., 80 percent of consumers said lost banking and financial data is a top concern. Lost security information (e.g., passwords) and identity information (e.g., passports or driving license) was cited as a concern of 76 percent of the respondents. An alarming statistic for companies that deal with consumer data is the 62 percent of the respondents to the RSA report who say they would blame the company for their lost data in the event of a breach, not the hacker. The report’s authors concluded that, “As consumers become better informed, they expect more transparency and responsiveness from the stewards of their data.”
Lack of trust in how companies treat their personal information has led some consumers to take their own countermeasures. According to the report, 41 percent of the respondents said they intentionally falsify data when signing up for services online. Security concerns, a wish to avoid unwanted marketing, or the risk of having their data resold were among their top concerns.
The report also shows that consumers will not easily forgive a company once a breach exposing their personal data occurs. Seventy-two percent of US respondents said they would boycott a company that appeared to disregard the protection of their data. Fifty percent of all respondents said they would be more likely to shop at a company that could prove it takes data protection seriously.
“As businesses continue their digital transformations, making greater use of digital assets, services, and big data, they must also be accountable for monitoring and protecting that data on a daily basis,” concluded the report.
Any company that stores or processes personal information about EU citizens within EU states must comply with the GDPR, even if they do not have a business presence within the EU. Specific criteria for companies required to comply are:
A new survey conducted by Propeller Insights and sponsored by Netsparker Ltd. asked executives which industries would be most affected by GDPR. Most (53 percent) saw the technology sector being most impacted followed by online retailers (45 percent), software companies (44 percent), financial services (37 percent), online services/SaaS (34 percent), and retail/consumer packaged goods (33 percent).
Who within my company will be responsible for compliance?The GDPR defines several roles that are responsible for ensuring compliance: data controller, data processor and the data protection officer (DPO). The data controller defines how personal data is processed and the purposes for which it is processed. The controller is also responsible for making sure that outside contractors comply. Data processors may be the internal groups that maintain and process personal data records or any outsourcing firm that performs all or part of those activities. The GDPR holds processors liable for breaches or non-compliance. It’s possible, then, that both your company and processing partner such as a cloud provider will be liable for penalties even if the fault is entirely on the processing partner.
The GDPR requires the controller and the processor to designate a DPO to oversee data security strategy and GDPR compliance. Companies are required to have a DPO if they process or store large amounts of EU citizen data, process or store special personal data, regularly monitor data subjects, or are a public authority. Some public entities such as law enforcement may be exempt from the DPO requirement. According to the Propeller Insights survey, 82 percent of responding companies say they already have a DPO on staff, although 77 percent plan to hire a new or replacement DPO prior to the May 25 deadline. That hiring doesn’t stop with the DPO. About 55 percent of the survey’s respondents reported that they had recruited at least six new employees to achieve GDPR compliance.
The GDPR places equal liability on data controllers (the organization that owns the data) and data processors (outside organizations that help manage that data). A third-party processor not in compliance means your organization is not in compliance. The new regulation also has strict rules for reporting breaches that everyone in the chain must be able to comply with. Organizations must also inform customers of their rights under GDPR.
What this means is that all existing contracts with processors (e.g., cloud providers, SaaS vendors, or payroll service providers) and customers need to spell out responsibilities. The revised contracts also need to define consistent processes for how data is managed and protected, and how breaches are reported. “The largest exercise is on the procurement side of the house—your third-party vendors, your sourcing relationships that are processing data on your behalf,” says Mathew Lewis, global head of banking and regulatory practice at legal service provider Axiom. “There’s a whole grouping of vendors that have access to this personal data and GDPR lays out very clearly that you need to ensure that all of those third parties are adhering to GDPR and processing the data accordingly.”
Client contracts also need to reflect the regulatory changes, says Lewis. “Client contracts take a number of different forms, whether they are online click-throughs or formal agreements where you make commitments to how you view, access, and process data.” Before those contracts can be revised, business leaders, IT, and security teams need to understand how the data is stored and processed and agree on a compliant process for reporting. “A pretty sizable exercise is required by the technology groups, the CISO, and data governance team to understand what data fits within the firm, where it’s being stored or processed, and where it’s being exported outside the company. Once you understand those data flows and the impact on the business, you can start to identify the vendors you need to be most focused on both from an information security perspective, how you manage those relationships going forward, and how you memorialize that in the contract itself,” says Lewis.
The GDPR might also change the mindset of business and security teams toward data. Most companies see their data and the processes they use to mine it as an asset, but that perception will change, says Lewis. “Given GDPR’s explicit consent and firms needing to be much more granular in their understanding of data and data flows, there’s a whole set of liabilities that now exist with the accumulation of data,” says Lewis. “That’s quite a different frame of mind both for legal and compliance, but maybe more important for the way the business thinks about the accumulation and usage of that data and for information security groups and how they think about managing that data.” “Data is leaving the firm in all kinds of ways,” says Lewis. “While the CISO and the technology groups need to be able to track all of that, you also need to put protection in place.” Those protections need to be spelled out in the contract so the outside firms understand what they can and cannot do with the data.
Lewis notes that by going through the process of defining obligations and responsibilities, it prepares a company to handle GDPR compliance operationally. “If one of your vendors says, ‘You were hacked last night,’ did they know who to call and how to respond as part of meeting the regulatory requirements,” he says. The 72-hour reporting window that the GDPR requires makes it especially important that vendors know how to properly report a breach. “If a vendor was hacked and you’re one of thousands of clients, do they notify your procurement department or an account person or someone in accounts receivables? It could come in all kinds of ways,” says Lewis. You want a clearly defined path in the contract for the information to get to the person in your organization responsible for reporting the breach. “A regulator is not going to say you shouldn’t have had a breach. They are going to say you should have had the policies, procedures, and response structure in place to solve for that quickly,” says Lewis. Larger companies might have thousands of contracts to update. Complicating that challenge is that it needs to be done late in the compliance process. Before you can define responsibilities and responsibilities, you must know exactly what data you have, where and how it is processed, and the data flows. “That’s left a lot of institutions racing toward the deadline trying to complete the technical and operational issues and having to play catch-up on putting the right contract in place to enforce that. A lot of firms have not done any renegotiation of contract terms.”
Patch management is the process that helps acquire, test and install multiple patches (code changes) on existing applications and software tools on a computer, enabling systems to stay updated on existing patches and determining which patches are the appropriate ones. Managing patches thus becomes easy and simple.
Patch Management is mostly done by software companies as part of their internal efforts to fix problems with the different versions of software programs and also to help analyze existing software programs and detect any potential lack of security features or other upgrades.
Software patches help fix those problems that exist and are noticed only after the software's initial release. Patches mostly concern security while there are some patches that concern the specific functionality of programs as well.
Patch management process features to detect missing patches, install the patches or hotfixes that are released from time to time, and provide instant updates on the latest patch deployment status.
Budget pressures continue to be high on IT organizations, and so automating day to day routine tasks is critical. Patch management software can be automated to enable all the computers to remain up-to-date with the recent patch releases from the application software vendors.
It is critical to take necessary steps to enhance the security posture of enterprises – large and small. Therefore, consistent patching of operating systems and applications with an automated patch management solution is important to mitigate and prevent security risks.
How does an Automated Patch Management Solution Work?
With automated Patch Management solution, each enterprise is equipped to update its endpoints with latest patches irrespective of what OS they run and where they are located.
Patching is a process to repair a vulnerability or a flaw that is identified after the release of an application or a software. Newly released patches can fix a bug or a security flaw, can help to enhance applications with new features, fix security vulnerability. Unpatched software can make the device a vulnerable target of exploits. Patching a software as and when the patch is released is critical to deny malware access. Patch Management Best Practices:
Some of the best practices of patch management that will allow the organizations to enhance cybersecurity are
Knowing why patch management is an important aspect of cybersecurity solution is critical. Quick response to latest patch updates would deny and protect vulnerable systems from zero-day threats.
Delayed patch application creates a severe impact causing major security breaches. The latest Wannacry attack revealed the vulnerability of not updating the software with patch fixes. The victims of Wannacry were those who delayed in updating the patch released by Windows to fix the SMB v1 protocol vulnerability – this resulted in loss of data, and business.
Managed service providers offer patch management software to fit the requirements of the business – big or small. MSPs take full control of the patch management process – while the businesses can focus on the management and revenue-generating aspects.
Some patches are incompatible with certain operating systems or applications and leads to system crashes. It is good for IT admins, to run a patch test before the patches are deployed on to the endpoint systems.
How do you know which patch management software is best for your organization?The demand varies from business to business, however there are few common traits, which most of the organizations look for in a patch management software.
A patch management software should be capable to:
If you are looking for a patch management solution that can offer all the above-mentioned features – ITarian offers efficient patch management solution with robust features to keep your network patched with the latest patch updates.
Software vendors release patches to fix vulnerabilities identified after the release of a software or application. Patch Management enables patch testing and deployment which is a critical aspect of cyber security. Quick and instant responses to patch updates would mitigate the chances of data breaches that can cause due to unpatched software. ITarian Patch Management software offers future-proof and scalable patch management solutions and strategies to protect and secure your business endpoints with quick and latest patch updates.
ITarian Patch Management allows you to: There’s a lot of software running in your organization, and none of it is flawless. Which means a lot of patches from multiple sources get released on an ad hoc basis, Patch Tuesday notwithstanding. You can’t simply wait to deploy patches when it’s convenient, because leaving those security flaws and major bugs unpatched leaves your business vulnerable. And while managing patches can be complex and tedious, the alternative of getting hit with a security breach is infinitely worse.
ITarian Patch Management allows you to:
Our industry-leading patch management operation team monitors key sources of patch intelligence—including Microsoft, Microsoft Security Bulletin, application vendors, CVE, automated crawler systems, and more—to identify the updates relevant for your environment.
Provides a real-time view of your network via automatic discovery of all managed endpoints to identify installed and/or missing security patches and detect vulnerabilities.
Protecting Cardholder Data with PCI Security Standards The twentieth century U.S. criminal Willie Sutton was said to rob banks because “that’s where the money is.” The same motivation in our digital age makes merchants the new target for financial fraud. Occasionally lax security by some merchants enables criminals to easily steal and use personal consumer financial information from payment card transactions and processing systems. It’s a serious problem – more than 510 million records with sensitive information have been breached since January 2005, according to PrivacyRights.org. As a merchant, you are at the center of payment card transactions so it is imperative that you use standard security procedures and technologies to thwart theft of cardholder data. Merchant-based vulnerabilities may appear almost anywhere in the card-processing ecosystem including point-of-sale devices; personal computers or servers; wireless hotspots or Web shopping applications; in paper-based storage systems; and unsecured transmission of cardholder data to service providers. Vulnerabilities may even extend to systems operated by service providers and acquirers, which are the financial institutions that initiate and maintain the relationships with merchants that accept payment cards .Compliance with the Payment Card Industry (PCI) Data Security Standard (DSS) helps to alleviate these vulnerabilities and protect cardholder data.
The intent of this PCI DSS is to help you understand the PCI DSS and to apply it to your payment card transaction environment. There are three ongoing steps for adhering to the PCI DSS: Assess — identifying cardholder data, taking an inventory of your IT assets and business processes for payment card processing, and analyzing them for vulnerabilities that could expose cardholder data. Remediate — fixing vulnerabilities and not storing cardholder data unless you need it. Report — compiling and submitting required remediation validation records (if applicable), and submitting compliance reports to the acquiring bank and card brands you do business with. PCI DSS follows common sense steps that mirror best security practices. The DSS globally applies to all entities that store, process or transmit cardholder data. PCI DSS and related security standards are administered by the PCI Security Standards Council, which was founded by American Express, Discover Financial Services, JCB International, MasterCard Worldwide and Visa Inc. Participating Organizations include merchants, payment card issuing banks, processors, developers and other vendors.
PCI Security Standards Include:
PCI Data Security Standard (DSS) The PCI DSS applies to all entities that store, process, and/or transmit cardholder data. It covers technical and operational system components included in or connected to cardholder data. If you are a merchant who accepts or processes payment cards, you must comply with the PCI DSS. PIN Transaction Security (PTS) Requirements The PCI PTS (formerly PCI PED) is a set of security requirements focused on characteristics and management of devices used in the protection of cardholder PINs and other payment processing related activities. The requirements are for manufacturers to follow in the design, manufacture and transport of a device to the entity that implements it. Financial institutions, processors, merchants and service providers should only use devices or components that are tested and approved by the PCI SSC . Payment Application Data Security Standard (PA-DSS) The PA-DSS is for software developers and integrators of payment applications that store, process or transmit cardholder data as part of authorization or settlement when these applications are sold, distributed or licensed to third parties. Most card brands encourage merchants to use payment applications that are tested and approved by the PCI SSC. Validated applications are listed at:
PCI certification ensures the security of card data at your business through a set of requirements established by the PCI SSC. These include a number of commonly known best practices, such as:
In addition, businesses must restrict access to cardholder data and monitor access to network resources.
PCI-compliant security provides a valuable asset that informs customers that your business is safe to transact with. Conversely, the cost of noncompliance, both in monetary and reputational terms, should be enough to convince any business owner to take data security seriously.
A data breach that reveals sensitive customer information is likely to have severe repercussions on an enterprise. A breach may result in fines from payment card issuers, lawsuits, diminished sales and a severely damaged reputation.
After experiencing a breach, a business may have to cease accepting credit card transactions or be forced to pay higher subsequent charges than the initial cost of security compliance. The investment in PCI security procedures goes a long way toward ensuring that other aspects of your commerce are safe from malicious online actors.
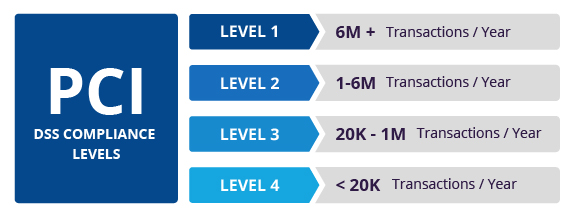
PCI compliance is divided into four levels, based on the annual number of credit or debit card transactions a business processes. The classification level determines what an enterprise needs to do to remain compliant.
The PCI SSC has outlined 12 requirements for handling cardholder data and maintaining a secure network. Distributed between six broader goals, all are necessary for an enterprise to become compliant.

1. A firewall configuration must be installed and maintained
2. System passwords must be original (not vendor-supplied)
Secure cardholder data
3. Stored cardholder data must be protected
4. Transmissions of cardholder data across public networks must be encrypted
5. Anti-virus software must be used and regularly updated
6. Secure systems and applications must be developed and maintained
7. Cardholder data access must be restricted to a business need-to-know basis
8. Every person with computer access must be assigned a unique ID
9. Physical access to cardholder data must be restricted
10. Access to cardholder data and network resources must be tracked and monitored
11. Security systems and processes must be regularly tested
12. A policy dealing with information security must be maintained
Since its formation, PCI DSS has gone through several iterations in order to keep up with changes to the online threat landscape. While the basic rules for compliance have remained constant, new requirements are periodically added.
One of the more significant of these additions was Requirement 6.6, introduced in 2008. It was established to secure data against some of the most common web application attack vectors, including SQL injections, RFIs and other malicious inputs. Using such methods, perpetrators can potentially gain access to a host of data—including sensitive customer information.
Satisfying this requirement can be achieved either through application code reviews or by implementing a web application firewall (WAF). The first option includes a manual review of web application source code coupled with a vulnerability assessment of application security. It requires a qualified internal resource or third party to run the review, while final approval must come from an outside organization. Moreover, the designated reviewer is required to stay up-to-date on the latest trends in web application security to ensure that all future threats are properly addressed.
Alternately, businesses can safeguard against application layer attacks by using a WAF, deployed between the application and clients. The WAF inspects all incoming traffic and filters out malicious attacks.
Offered byVajenthura, our cloud-based WAF blocks web application attacks using a number of different security methodologies, including signature recognition and IP reputation. Being fully compliant with PCI Requirement 6.6, it can be configured and ready to use within minutes. To make compliance even easier, theVajenthura cloud WAF doesn’t require any hardware installation or management overhead. This enables all organizations—from large companies to startups and small and medium enterprises, which may not have the requisite security infrastructure and staff—to remain protected and PCI DSS compliant.
As the demand for your company’s services increase, so do the requests from your customers for assurance. Assurance, that you’ve taken the steps necessary to protect the privacy and confidentiality of their data as well as the security, availability and processing integrity of your systems. You are not alone. Looking to reduce infrastructure costs, many organizations are utilizing outsourcing and cloud computing solutions. Similarly, the demand for assurance of the integrity of these outsourced applications and functions has expanded as well.
As a service organization providing outsourced or cloud computing, you are an extension of your customers’ system of internal control and your customers rely upon you to protect them from the risk of fraud, unauthorized use of data, loss of data and violation of privacy. The American Institute of Certified Public Accountants (AICPA) has provided the solution to demonstrate the reliability of your system of controls and to provide assurance to your customers by providing three Service Organization Control (SOC) reporting options, SOC 1, SOC 2 and SOC 3.
SOC 1 reports address controls at a service organization that are likely to be relevant to an audit of a customer’s financial statements. A Service Organization Control, or SOC 1 report, is a formal audit of a service provider’s controls that affects their customer’s internal control over financial reporting. SOC 1 reports, often referred to by the AICPA attestation standards as SAS 70 and SSAE 16 (now SSAE 18), are specifically intended to meet the requirements of the entities that use service organizations and those entities’ financial statement auditors.
Effective May of 2017, the SSAE 18 attestation standard superseded SSAE 16. This update is intended to help simplify and unify international attestation standards. Most requirements remained the same, however, some key changes include:
• Stronger focus on Risk Assessment • Emphasis on Vendor Management Programs • Monitoring subservice organizations • Modifications to the written assertion requirements of management
There are two types of SOC 1 reports:
• Type 1 – This report shows customers and their auditors that your organization’s systems and controls are accurately described, that the controls are in place, and that those controls are designed to fulfill your financial control objectives as of a specified date.
• Type 2 – This report provides the same information as the Type 1 report, while also verifying that the controls properly operate, providing a description of the tests auditors performed to determine that information, and the results of those tests over a specified period.
Obtaining a third party SOC 1 attestation report adds significant value to your organization and also provides your customers with an increased level of confidence. It sets you apart from the competition by demonstrating your commitment to the security of your customer’s data and information.
SOC 2 and SOC 3 reports address controls at a service organization related to operations and compliance as identified in the AICPA’s Trust Service Principles. A SOC 2 report provides service organizations with an opinion on controls that are related to a predefined set of principles. Unlike a SOC 1 report, where control objectives and controls are specified to the industry and unique processes within a company, a SOC 2 report utilizes a standardized set of industry neutral controls based on the AICPA’s Trust Services Principles — security, availability, processing integrity, confidentiality and privacy. A SOC 2 report must include the security principle (known as the common criteria), with inclusion of the remaining four principles being optional based on the company’s needs.
There are two types of SOC 2 reports: • Type 1 – This report shows customers and their auditors that your organization’s systems and controls are accurately described, that the controls are appropriately designed and that those controls are in place as of a specified date, or point in time. • Type 2 – This report demonstrates to customers and their auditors that your organization’s systems and controls are accurately described, that the controls are appropriately designed, and include a description of tests performed to verify that the controls are operating effectively throughout a specified period of time.
Which Trust Services Principles should I select?
When selecting the Trust Services Principles that are right for your SOC 2 report, first determine the scope of the engagement and the principles most applicable to your system. The following high-level definitions can help get you thinking about which principles apply to your organization:
1. Security – The system is protected against unauthorized physical and logical access
2. Availability – The system is accessible, as determined by contract of service level agreement
3. Processing Integrity – System processing is complete, valid, accurate, timely, and authorized
4. Confidentiality – Information designated as confidential is protected as agreed
5. Privacy – Personal information is collected, used, retained, disclosed and destroyed with the commitments in the entity’s privacy notice and principles set forth by the AICPA
SOC 2 reports provide significant value in situations where customers and internal management must have confidence in the service organization’s system of controls to provide security, availability, processing integrity, confidentiality and privacy. In addition to addressing the internal needs, the SOC 2 report is valuable to your existing customers because it provides a CPA-signed report as assurance of your systems and processes.
The SOC 3 report is intended to be used as a marketing tool to an unrestricted expanded audience compared to that of a SOC 2 report.
The SOC 3 report is intended to be used as a marketing tool to an unrestricted expanded audience compared to that of a SOC 2 report, such as potential customers, investors, etc. Similar to a SOC 2 report the SOC 3 report provides an opinion on controls relevant to one or more of the Trust Service Principles (TSP). The SOC 3 report is unique in its lack of use restrictions and the use of a SOC 3 seal to be used on your website making it the perfect marketing tool for customers that must have confidence in the service organization’s system of controls to provide security, availability, processing integrity, confidentiality and privacy.